Enterprise-Grade Cybersecurity Assessments for Small, Mid-Sized, and Large Organizations
Take Control of Your Cybersecurity with a Clear, Actionable Assessment
Whether you have a small business, a growing mid-market operation, or a large enterprise, unseen vulnerabilities may be putting your company at risk. You want to protect your business, meet compliance requirements, and avoid costly breaches. We help you get there with unbiased, enterprise-grade cybersecurity audits led by ISACA-certified experts.
Common Challenges You Face:
- ❌ Inconsistent security controls and policy enforcement
- ❌ Legacy systems and weak access controls
- ❌ Cloud and SaaS misconfiguration and exposed data
- ❌ Shadow IT and vendor risk
- ❌ Compliance gaps (HIPAA, PCI-DSS, NIST 800-171, SOC 2)
- ❌ Disaster recover plans that don't hold up under pressure
We Help You Solve These Problems With:
- A clear risk register with likelihood, impact, and assigned owners
- Prioritized recommendations for near-term risk reduction and phased improvements (sequenced by risk, effort, and business impact)
- Compliance gap analysis tailored to your industry
- Vendor-neutral advice on tools and training
- Executive-ready reports you can act on immediately
Talk to a Cybersecurity Consultant
A Comprehensive Cybersecurity Assessment Tailored to You:
We evaluate your security posture across key domains to give you a complete picture:
- Network & Infrastructure Security: Architecture, segmentation, firewall rules, intrusion prevention
- Identity & Access Management: Authentication, privileged access, MFA adoption
- Endpoint & Device Security: Patch management, EDR/XDR posture, device encryption
- Cloud & SaaS Security: Microsoft 365, AWS, Google Cloud configurations, and governance
- Data Protection & Privacy: Encryption, backups, retention policies, DLP, sensitive data handling
- Compliance Readiness: HIPAA, PCI-DSS, NIST CSF/800-53, SOC 2, CJIS, (and other applicable frameworks)
- Incident Response Preparedness: Incident Response plan validation, tabletop exercises, recovery testing readiness
- Security Awareness & Training: Phishing simulation insights, role-based training needs
- Third-Party Risk: Vendor security posture, contractual requirements, ongoing monitoring
A Governance-First Audit That Respects Your Time
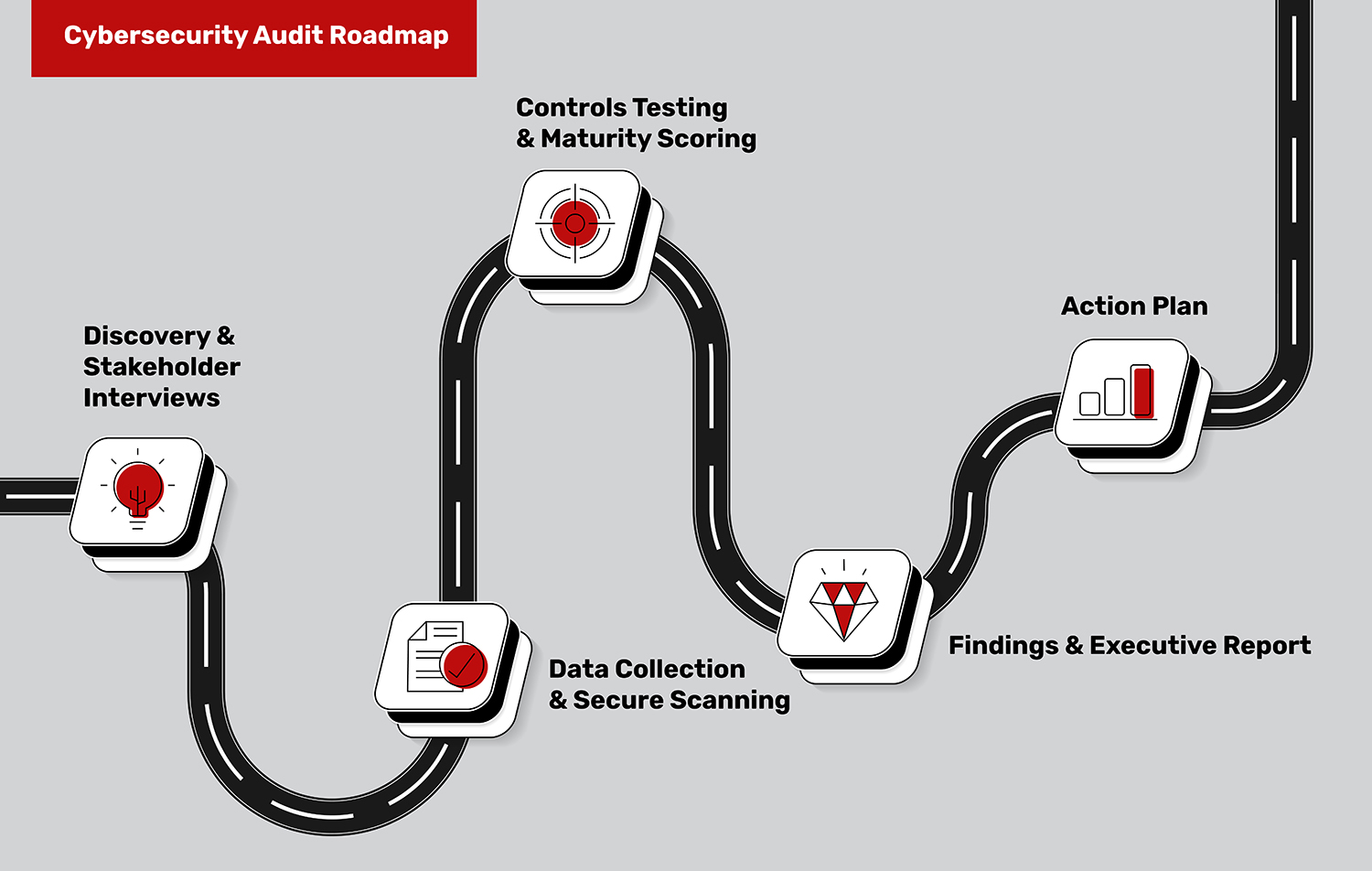
Our ISACA-certified auditors follow a structured, low-disruption process that combines interviews, secure discovery, and controls testing against globally recognized frameworks like NIST, COBIT, and CIS.
- Discovery & Stakeholder Interviews – Executives, business owners, IT/security teams
- Data Collection & Secure Scanning – Agent-based tools, configuration / documentation reviews
- Controls Testing & Maturity Scoring – Benchmarked to NIST/COBIT/CIS
- Findings & Executive Report – Non-technical summary report + technical details
- Action Plan – Prioritized recommendations with guidance on effort, sequencing, and budgetary ranges
What Will You Walk Away With? Actionable Intelligence. No Guesswork.
Once the cybersecurity audit is complete, you will receive:
- A security scorecard and posture model
- Onsite or virtual findings presentation
- Executive summary and technical report
- Key themes from stakeholder interviews
- Clear recommendations and solution options
- Supporting artifacts like diagrams and inventories
Cybersecurity Expertise Trusted by Leaders in High-Risk and Regulated Industries
- Construction, Architecture & Engineering: Secure mobility, workflow protection
- Healthcare: HIPAA, PHI protection, EHR integrations, DR/BCP
- Financial Services: SOC 2, GLBA, fraud prevention, vendor risk
- Legal: Client confidentiality, eDiscovery, matter-centric security
- Government/ & Public Sector: NIST/CJIS alignment, procurement readiness
- Manufacturing & Distribution: OT/ICS security, IoT/edge devices
Scarlett Group is Your Trusted Guide in Cybersecurity.
We’re not here to sell products—we’re here to help you grow your business. From SMBs to enterprises, Scarlett Group equips you with a strategic cybersecurity assessment and a tailored action plan—no bias, just results.
Real Results from Real Clients
CASE STUDY: Public Sector Organization Concerned About Cybersecurity Vulnerabilities
A public sector organization facing uncertainty around its cybersecurity posture partnered with Scarlett Group to gain strategic clarity. Following NIST Cybersecurity Framework, Scarlett Group’s assessment provided leadership with a clear understanding of the organization’s cyber risk profile, enabling informed decisions and proactive risk management. The strategic roadmap aligned cybersecurity investments with business objectives, improving resilience against ransomware and readiness for cyber liability insurance.
